What is Private Proving?
Private Proving is a method of generating cryptographic proofs inside a Trusted Execution Environment (TEE) that ensures input data (the witness) remains completely confidential during proof generation. This means neither the verifier nor the prover can see an application’s input data.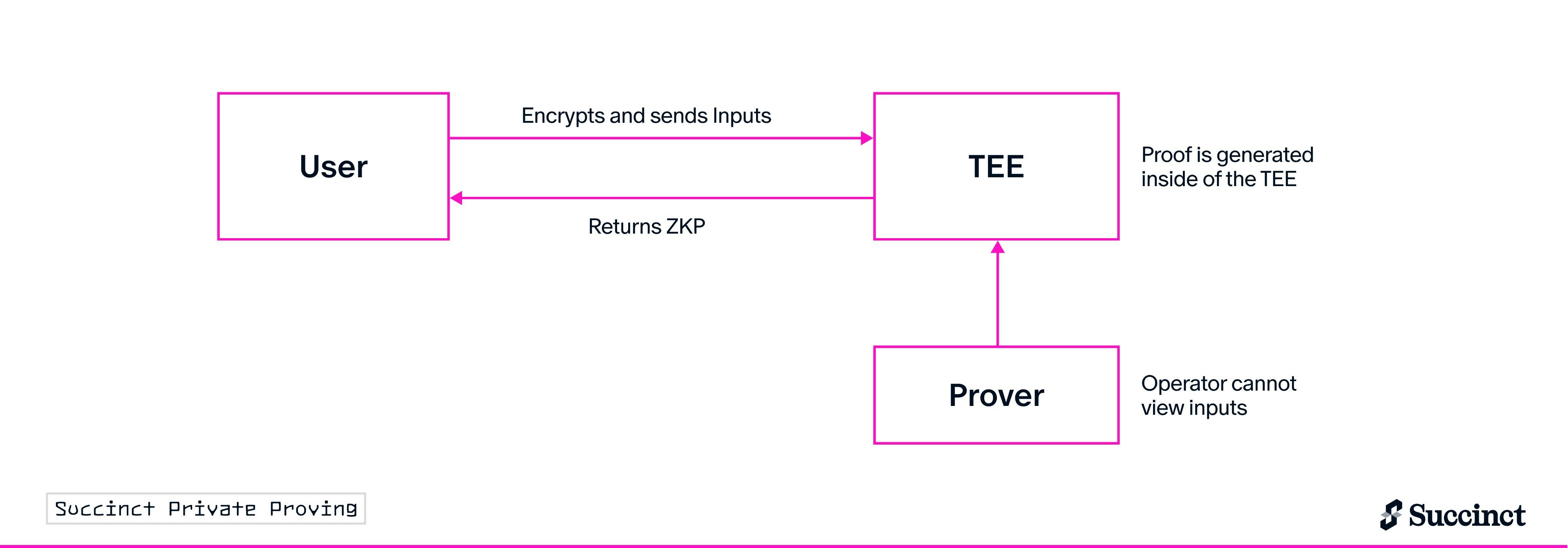
The Problem: Witness Data Exposure in Traditional ZK Proving
Traditional zero-knowledge proving systems verify computation correctness, but the witness data (private inputs) is exposed to the prover operator during proof generation:- Privacy-focused rollups: Prover operators can see user transaction amounts, recipients, and trading strategies
- Private DeFi protocols: Witness data includes sensitive positions, balances, and trading logic
- Confidential identity systems: User credentials and personal data are exposed to prover infrastructure
- Private payments: Transaction amounts and sender/receiver information visible to prover
The Solution: Run ZK Provers Inside TEE
Private proving runs the proof generation process inside hardware-isolated environments, ensuring witness data never leaves the secure enclave:- Witness data enters the TEE and remains hardware-encrypted throughout proving
- The zkVM (like SP1) executes inside the TEE to generate the proof
- Only the final proof leaves the TEE - witness data stays protected
- TEE attestation proves the proving environment was secure
- Complete Witness Privacy: No one, including the prover operator, can see witness data
- Hardware-Level Security: Data encrypted at the silicon level (Intel TDX, AMD SEV, AWS Nitro)
- Developer-Friendly: Write private applications in Rust using familiar zkVM frameworks
- Performance: GPU TEE (H200) provides hardware acceleration for fast proof generation
- Verifiable Security: Remote attestation cryptographically proves the secure execution environment
Learn more about Private Proving from Succinct Labs’ Private Proving announcement.
Benefits vs Traditional ZK
| Feature | Traditional ZK | Private Proving (ZK in TEE) |
|---|---|---|
| Proof Correctness | ✅ Cryptographic | ✅ Cryptographic |
| Witness Privacy | ❌ Exposed to prover | ✅ Hardware encrypted |
| Verifiable Execution | ❌ No guarantees | ✅ TEE attestation |
| Developer Experience | Circuit development | ✅ No code changes (Rust/zkVM) |
| Performance | Fast | Minimal overhead with GPU TEE |
| GPU Acceleration | ✅ Yes | ✅ Yes (H100/H200) |
| Trust Assumptions | Cryptography only | Cryptography + hardware |
Private Proving in Production
Phala Cloud: Hardware-Accelerated Private Proving
Phala Cloud provides production-ready infrastructure for private proving with GPU TEE:| 🚀Phala Network: Run zk-Rollup STF (state transition function) in TEE | Use-Cases-Multi-Proof.png | Phala SGXProver |
| 🔒Primus: Build Trustless zkTLS with TEE | tee_zktls.png | Primus zkTLS |
| 💾Running SP1 zkVM in TEE H200 with Low Overhead | zkvm-sp1-in-gpu-tee.jpg | SP1 zkVM in TEE |
Multi-Proof Systems: Defense-in-Depth (SP1-2FA)
While private proving protects data privacy, some applications require maximum security through defense-in-depth. Multi-proof systems like Succinct’s SP1-2FA generate both ZK and TEE proofs in parallel: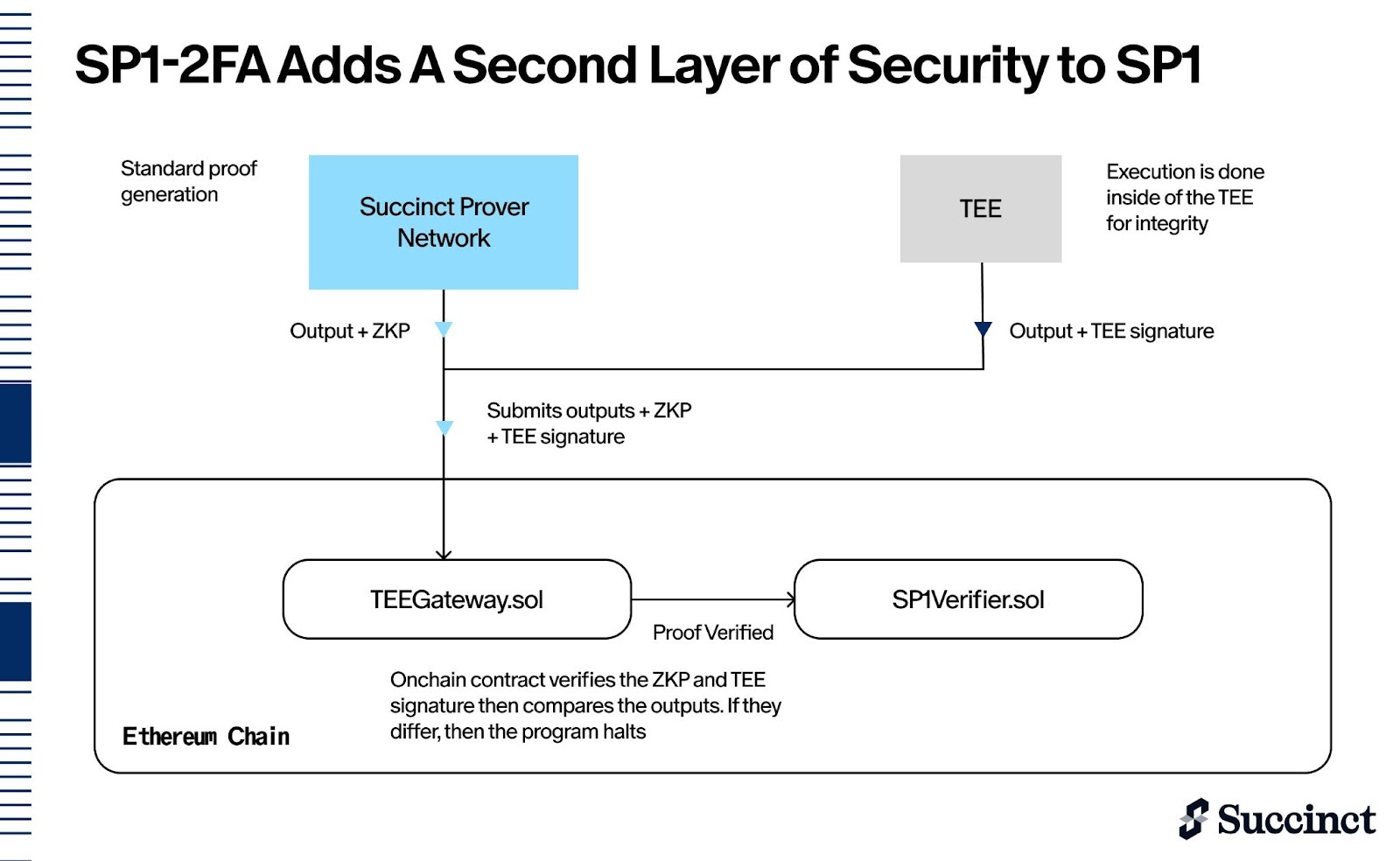
- Private Proving: ZK prover runs inside TEE (focus: data privacy)
- SP1-2FA: ZK and TEE run in parallel (focus: maximum security)
- Critical infrastructure (blockchain consensus, bridges)
- High-value DeFi protocols (significant TVL at risk)
- Defense against undiscovered ZK circuit bugs
- Regulatory requirements for multiple independent proofs
Learn more about SP1-2FA from Succinct’s blog post.
References and Further Reading
- Succinct Labs: Private Proving Blog Post | SP1-2FA Technical Details
- Vitalik Buterin: Multi-Proof Systems Presentation
- Justin Drake: 2FA ZK-Rollups with SGX
- Phala Network: SP1 zkVM Performance Benchmark

