What is the Trust Center?
The Trust Center is an automated verification platform that generates comprehensive security reports for every application deployed on Phala Cloud. It provides cryptographic proof that your application is running in a genuine TEE with the exact code you deployed, giving you and your users confidence in the integrity and security of your deployment.Automatic Verification: Every application deployed to Phala Cloud automatically receives a Trust Center verification report. No additional configuration required.
Why Trust Center Verification Matters
Traditional cloud platforms require you to trust the provider. With Phala Cloud and Trust Center:- Verify Hardware Authenticity: Cryptographically prove your app runs on genuine Intel TDX and Nvidia CC hardware
- Confirm Code Integrity: Verify the exact Docker compose configuration deployed matches your source code
- Validate OS Security: Ensure the operating system hasn’t been tampered with
- Prove Zero Trust: For gateway deployments, verify domain certificates are managed entirely within the TEE
- Regulatory Compliance: Meet GDPR, HIPAA, and other privacy requirements with verifiable evidence
- Customer Trust: Share public verification reports with users to prove data privacy
- Security Audits: Provide auditors with cryptographic proof of deployment integrity
Accessing Your Verification Report
Every Phala Cloud application receives a unique verification report URL:- The Phala Cloud dashboard
- The API response when creating a CVM
Understanding Your Verification Report
The Trust Center report displays comprehensive verification results across multiple security dimensions. Let’s walk through each section:Overview Section
The left column of the report shows your application’s basic information and overall verification status.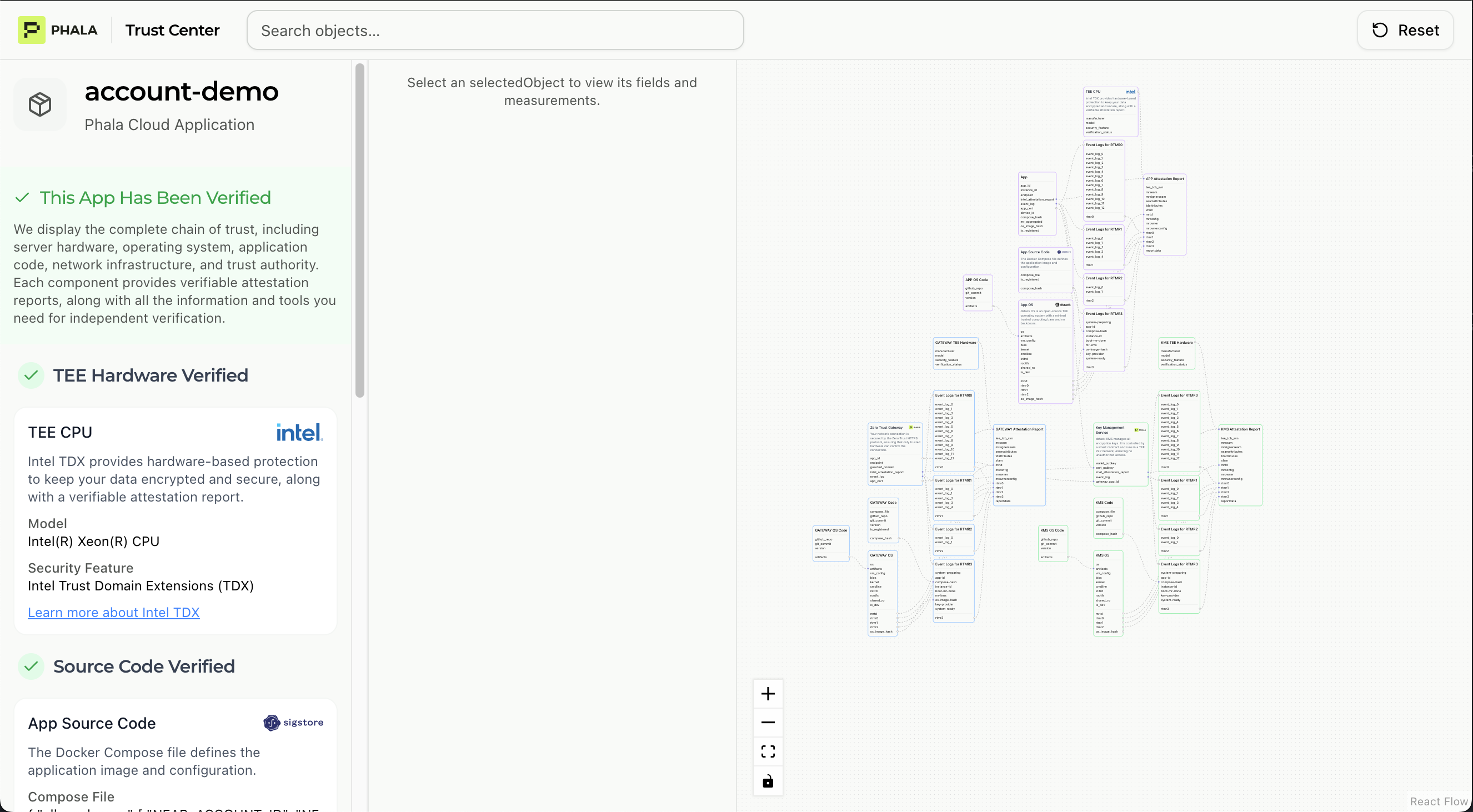
- App Name: Your application’s identifier (e.g., “account-demo”)
- Verification Status: Overall pass/fail indicator with green checkmark when all checks succeed
- Hardware Verification: Confirms TEE runs on genuine Intel TDX and Nvidia CC hardware
- Source Code Verification: Validates deployed Docker Compose matches your source code repository
- Network Verification: Checks domain certificates and network infrastructure security
- Operating System Verification: Ensures OS image matches trusted dstack release
- Key Management Verification: Validates cryptographic key derivation
Hardware Verification
This section proves your application runs on genuine Intel and Nvidia TEE hardware.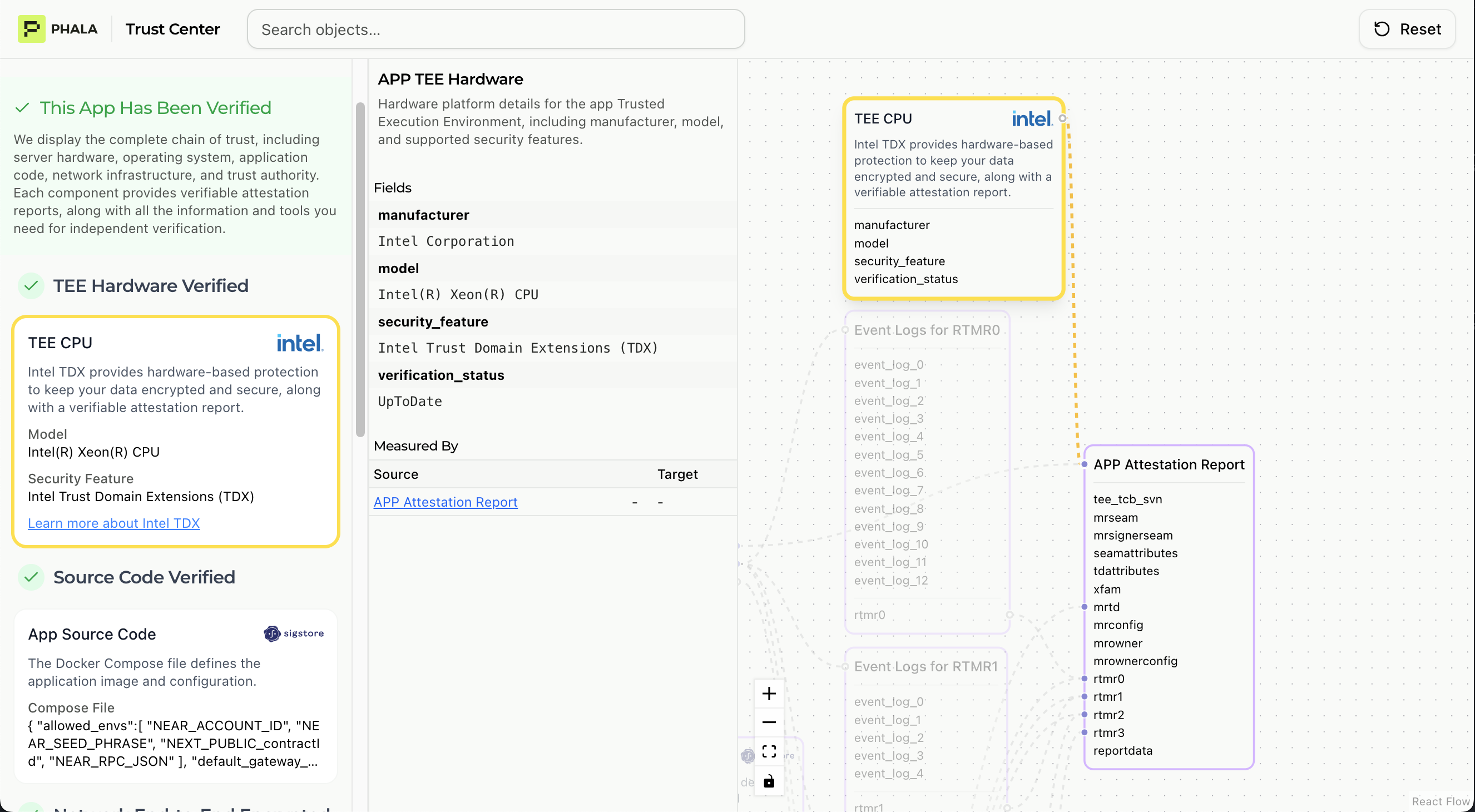
- Intel TDX Quote: Cryptographically signed attestation from Intel hardware
- (Optional) Nvidia CC Attestation Report: Cryptographically signed attestation from Nvidia hardware
- TCB Status: Trusted Computing Base security version (checks for known vulnerabilities)
- Platform Certificates: Validates certificate chain back to Intel/Nvidia root CA
- Hardware Identity: Confirms genuine Intel processor with TDX enabled and Nvidia GPU with CC enabled
Source Code Verification
This is the critical verification that your deployed application contains exactly the code you intended.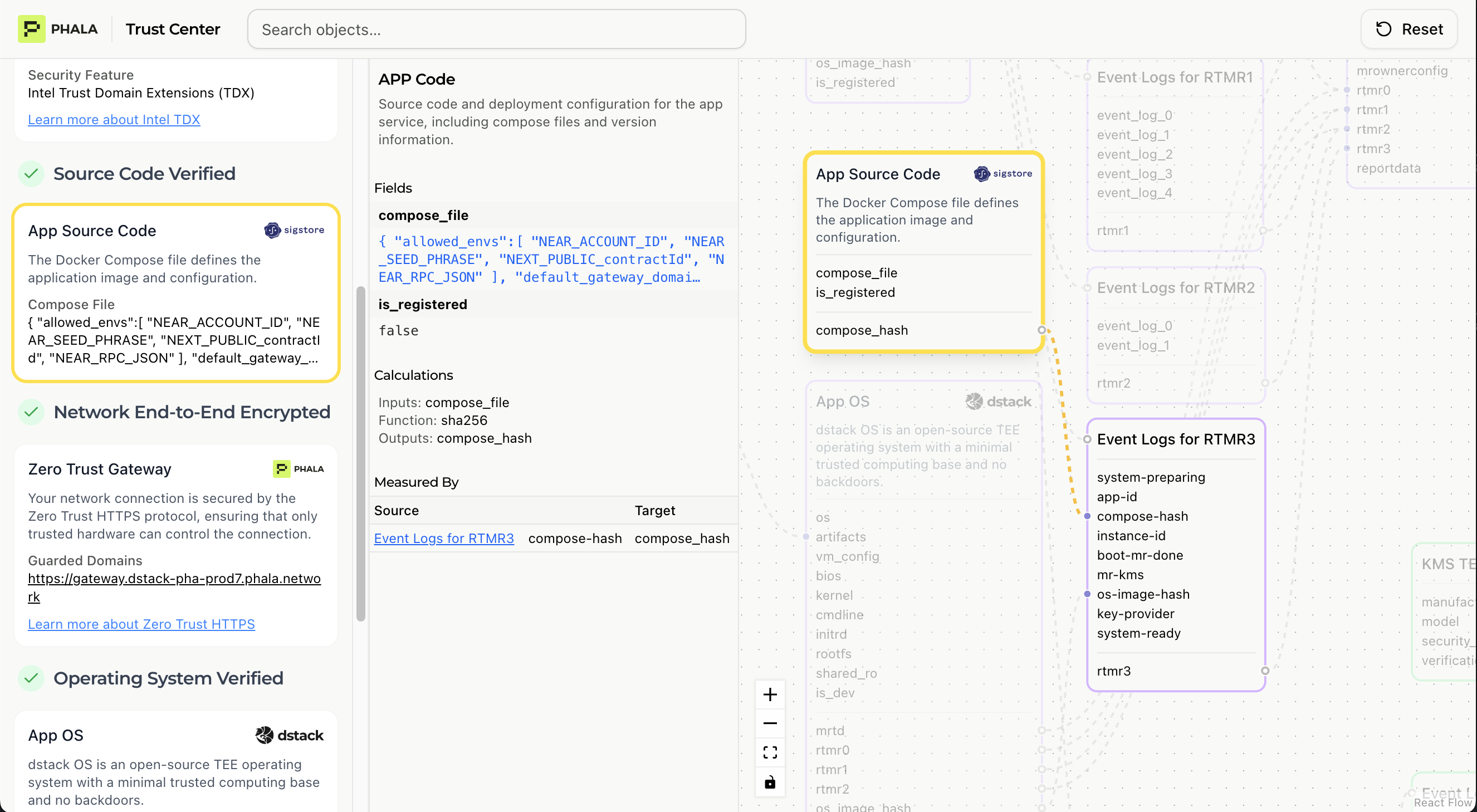
- Compose Hash: SHA256 hash of your configuration file containing the raw Docker compose file and other metadata
- RTMR3: Application-specific measurement register containing:
app-id: Application identifiercompose-hash: Hash of deployment manifestinstance-id: Specific deployment instanceos-image-hash: Hash of operating system image
Operating System Integrity
This verification confirms the OS running in your TEE matches a known trusted version.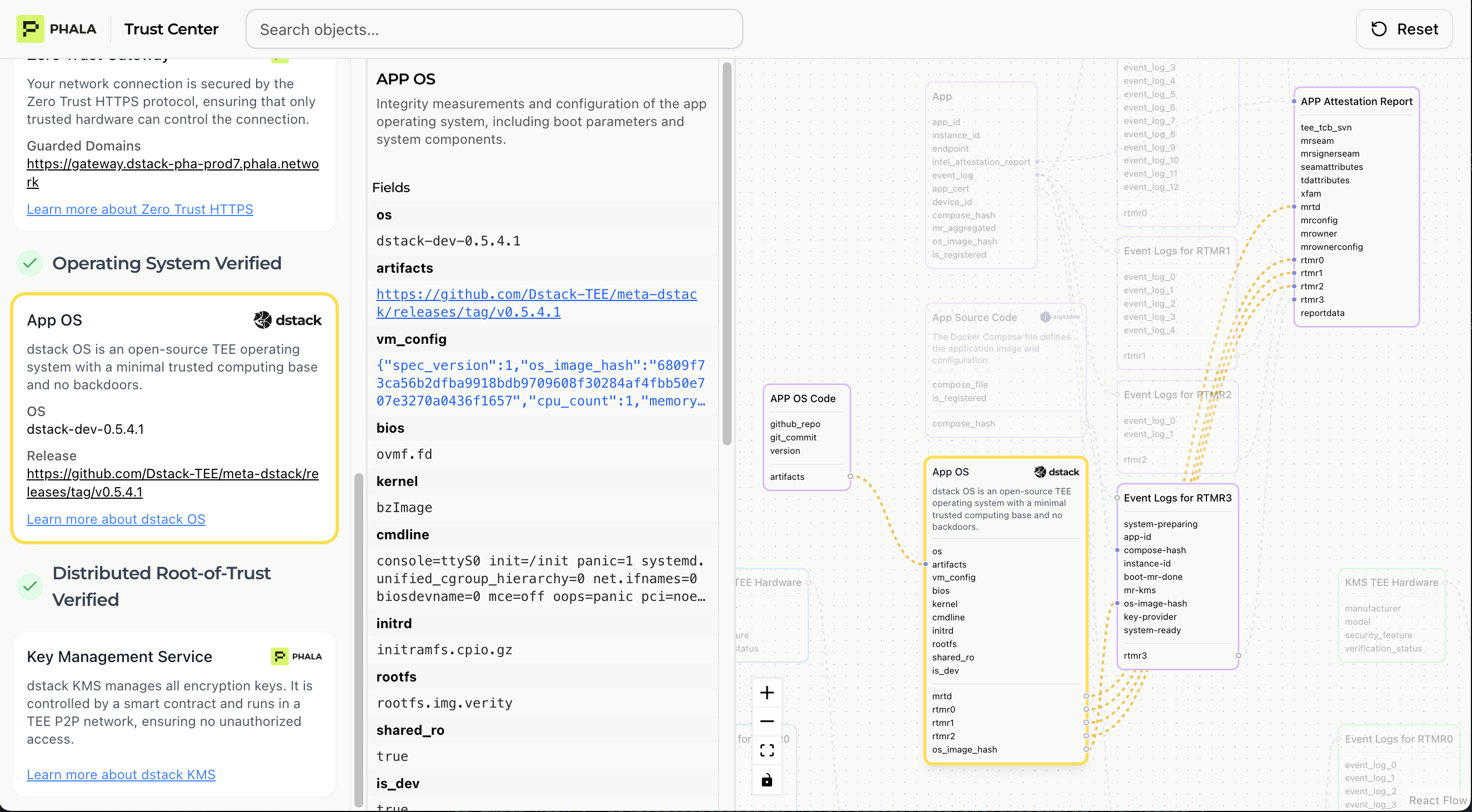
- MRTD (Measurement Root of Trust Domain): Hash of the initial TD state
- RTMR0: Virtual hardware environment measurement
- RTMR1: Linux kernel measurement
- RTMR2: Kernel command line and initrd measurement
- dstack Version: Specific OS image version hash
Network Verification (Gateway Deployments)
For applications exposed via custom domains with dstack-gateway, this verifies zero-trust HTTPS and secure traffic forwarding.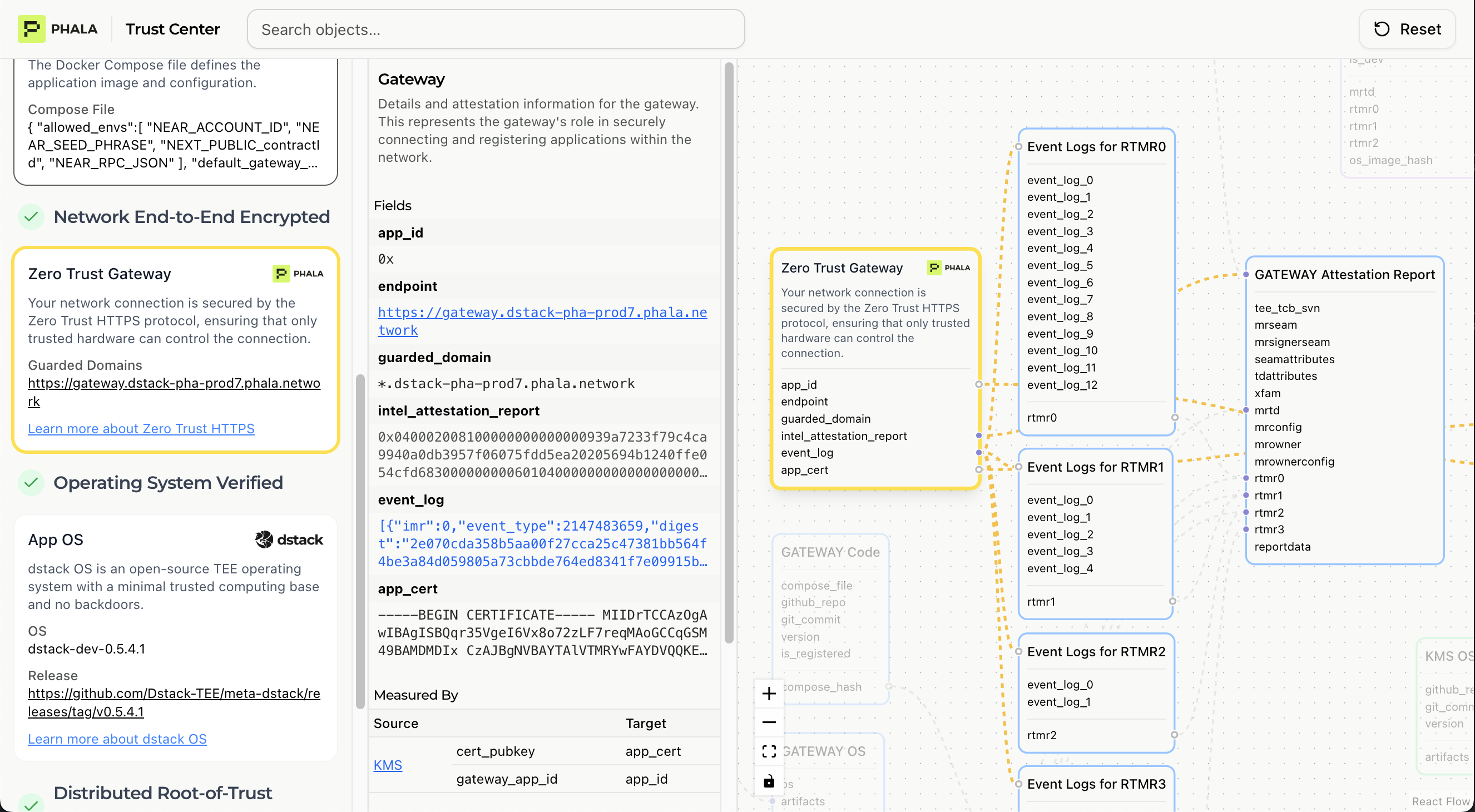
- Gateway TEE Status: Confirms the dstack-gateway itself runs in a TEE environment
- TLS Certificate: Certificate private key generated entirely within TEE
- CAA Records: DNS Certification Authority Authorization locked to TEE-controlled account
- Certificate Transparency: All certificates logged to public CT logs
- Domain Ownership: Cryptographic proof the domain is controlled by the TEE
Key Management Service Verification
This section verifies that cryptographic keys are properly managed and derived through Phala’s decentralized key management system.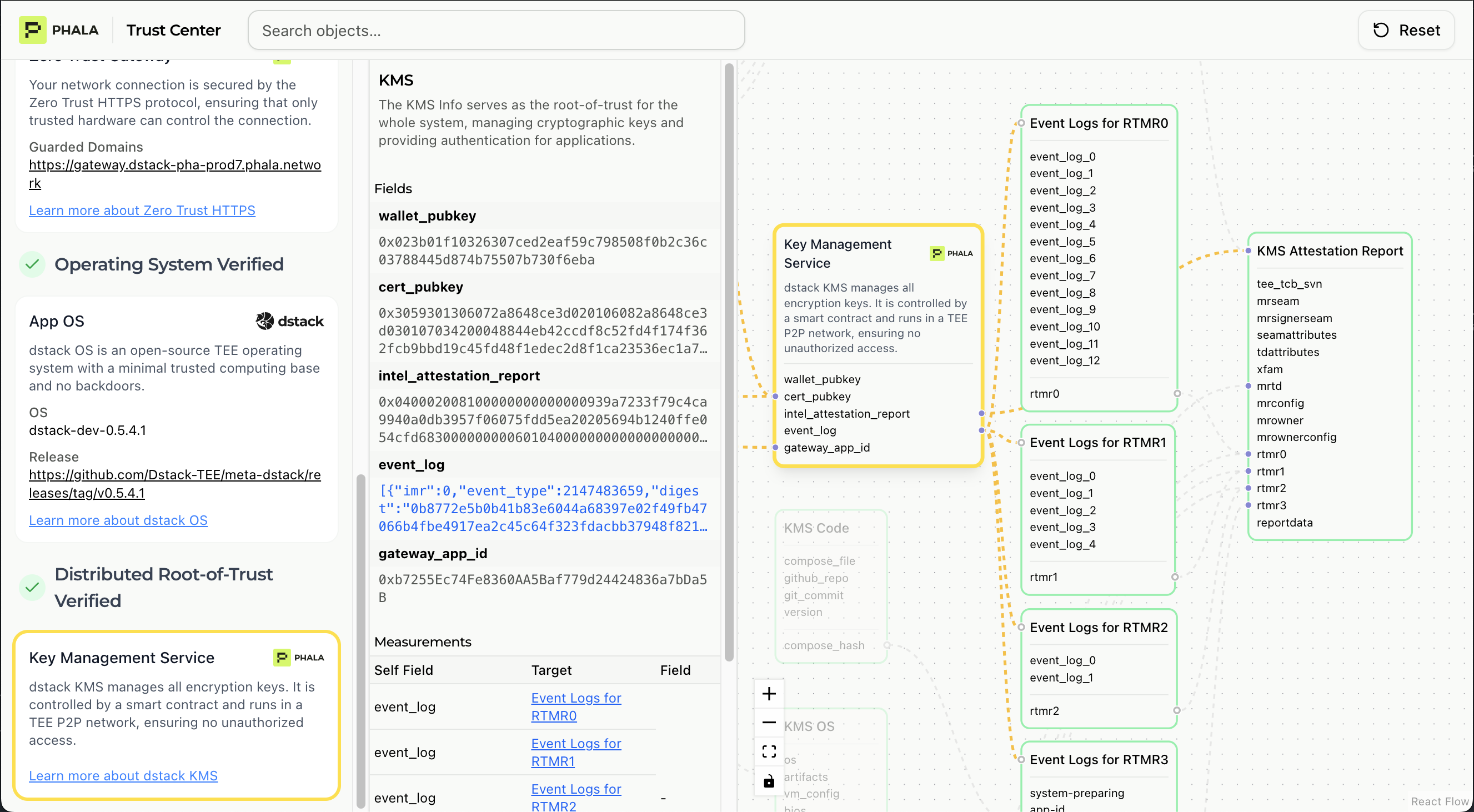
- Key Provider Address: The decentralized KMS endpoint used for key derivation
- KMS Node TEE Status: All KMS nodes run in TEE environments with program digests matching the smart contract
- App-ID Binding: Confirms keys are uniquely derived from your application identifier
- Key Derivation Protocol: Validates the cryptographic protocol used to generate encryption keys
- No Vendor Lock-in: Verifies keys can be recreated on any Phala worker or dstack node with the same app-id
Interpreting Verification Status
✅ Passed Verification
When all checks pass:- Your app runs on genuine Intel TEE hardware
- The OS matches a trusted dstack version
- Your source code hash matches the deployed version
- (If applicable) Domain certificates are TEE-controlled
⚠️ Partial Verification
Some checks passed, others failed or skipped:- Check which specific verifications failed
- Common causes: outdated TCB version, domain not configured, custom OS modifications
❌ Failed Verification
Verification could not complete:- Hardware attestation signature invalid
- Source code hash mismatch
- OS image not recognized
Sharing Your Verification Report
Trust Center reports are publicly accessible by design. This enables:- Customer Transparency: Share your report URL in documentation or marketing
- Auditor Access: Provide reports to security auditors without exposing credentials
- Automated Verification: Third parties can programmatically verify your deployment
Programmatic Verification
See Trust Center Technical Documentation for API details and integration examples.Trust Center vs Manual Verification
| Feature | Trust Center | Manual Verification |
|---|---|---|
| Ease of Use | ✅ Automatic, zero config | ❌ Complex, requires tooling |
| Public Auditability | ✅ Shareable URL | ⚠️ Must share raw quote data |
| Verification Speed | ✅ Seconds | ⚠️ Minutes to hours |
| Technical Expertise | ✅ No expertise needed | ❌ Requires cryptography knowledge |
| Blockchain Integration | ✅ Verifies onchain records | ⚠️ Manual registry lookup |
Next Steps
- Learn the Technical Details: Trust Center Technical Architecture
- Understand Attestation: Verifying TEE Attestation
- Deep Dive on Security: Security Architecture
Additional Resources
- Trust Center Platform: https://trust.phala.com
- GitHub Repository: https://github.com/Phala-Network/trust-center
- Example Report: account-demo verification

